Integrating Snort NIDS with Splunk
Written on May 12th, 2020 by Caitlin Allen
Halfway through the spring semester of my junior year, I was in Bergen, Norway with friends and my boyfriend. We were rushing to clean the Airbnb we were staying in and packing to get on our flight that was rebooked for the next day. Donald Trump had announced sometime after midnight in Norwegian time that we needed to be out of Europe so we would not face issues from the COVID-19 travel ban that was about to be implemented.
 Getting back into the United States, we learned that our schools were closing for the semester. I luckily still had my apartment in Vermont, I could comfortably work from home for my internship. However, my HP Proliant server was in my boyfriend’s dorm, and I needed my server so I could do this final project.
Getting back into the United States, we learned that our schools were closing for the semester. I luckily still had my apartment in Vermont, I could comfortably work from home for my internship. However, my HP Proliant server was in my boyfriend’s dorm, and I needed my server so I could do this final project.
We drove back to Vermont the second we could and asked for access to his dorm to get it and some clothes for what we thought would be only a month or two. My final project was now saved from the lack of RAM being provided in our class environments and the disaster my partner and I’s environments had become with misconfigurations and firewalls we lost track of during our extended spring break.\
So, after the disaster of COVID-19, setting up a server under my bed in my apartment, and trying to coordinate this project over Discord and FaceTime, heres what we did.
Whats Snort? If you’ve never heard of it, its a free and open-source intrusion detection and prevention system that was created in 1998 by Martin Roesch. Snort started as a sniffer that Roesch wrote when he got into security in the mid 90’s. The sniffer was released as an open-source project to not only give Roesch suggestions, but to also help him debug what he was writing. It started to become a bit more than a sniffer and becoming an IDS.
Snort has a few modes to run as, for our project, we’ll be using Network Intrusion Detection System (NIDS) mode. Since we need Snort rules, we decided to download the Community Ruleset but we’ll be making our own. The rule structure is not too hard to follow once you understand it!
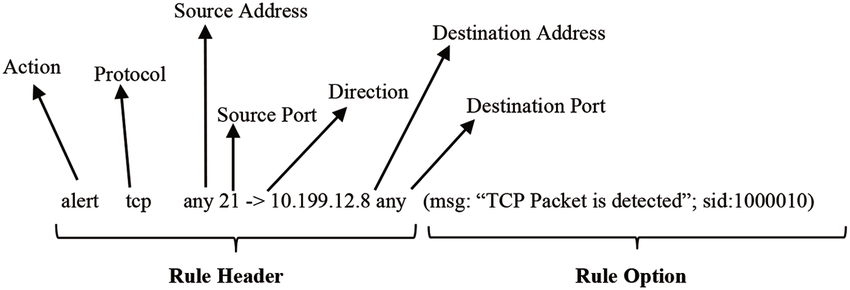
Snort logs also are output in a few different ways, for our environment, we used the alert_syslog format. In the attached documentation theres a bit more on Snort log format. We used the alert_syslog format since these ship to syslog, which is where Splunk will be pulling logs from.
If you work in SOC, you are most likely familiar with Splunk. This security information and event management (SIEM) tool is a favorite of mine. This project was powered by a 30 day free trial of Splunk Enterprise, and with the free trial we got to play around with Splunk’s capabilities after which was fun!

A cool tool we got to play around with was Mutillidae. This is a deliberately vulnerable web-app that we got to not only practice our skills with, but also monitor traffic from. Mutillidae lets you perform all different vulnerabilities and challenges for the user, letting them test out their web app skills. Prior to this, I’ve only used the Damn Vulnerable Web App so I was familiar with how a purposely made vulnerable web app would look, but I’ve never actually watched web traffic from one of these. Next semester I’ll be taking a Network Forensics & Threat Hunting class on top of beginning an internship in SOC and Threat Intelligence, so I got to explore whats up ahead for me with this project!
In our environment, for simplicity reasons, as well as project requirements, we created a segmented network consisting of 2 VyOS firewalls, one guarding a network called MGMT where Splunk sat behind, and one guarding our WAN where a Windows host was located. This Windows host was actually how my partner was accessing the network since we had to let him in through TeamViewer. Normally we would port forward but my roommate didn’t know the router password and because we constantly needed it for work or school, resetting it was just not ideal at the time (its been reset now!). We also had a LAN network with an Ubuntu Workstation and our DMZ with a host running Snort and a box called web also using Ubuntu.
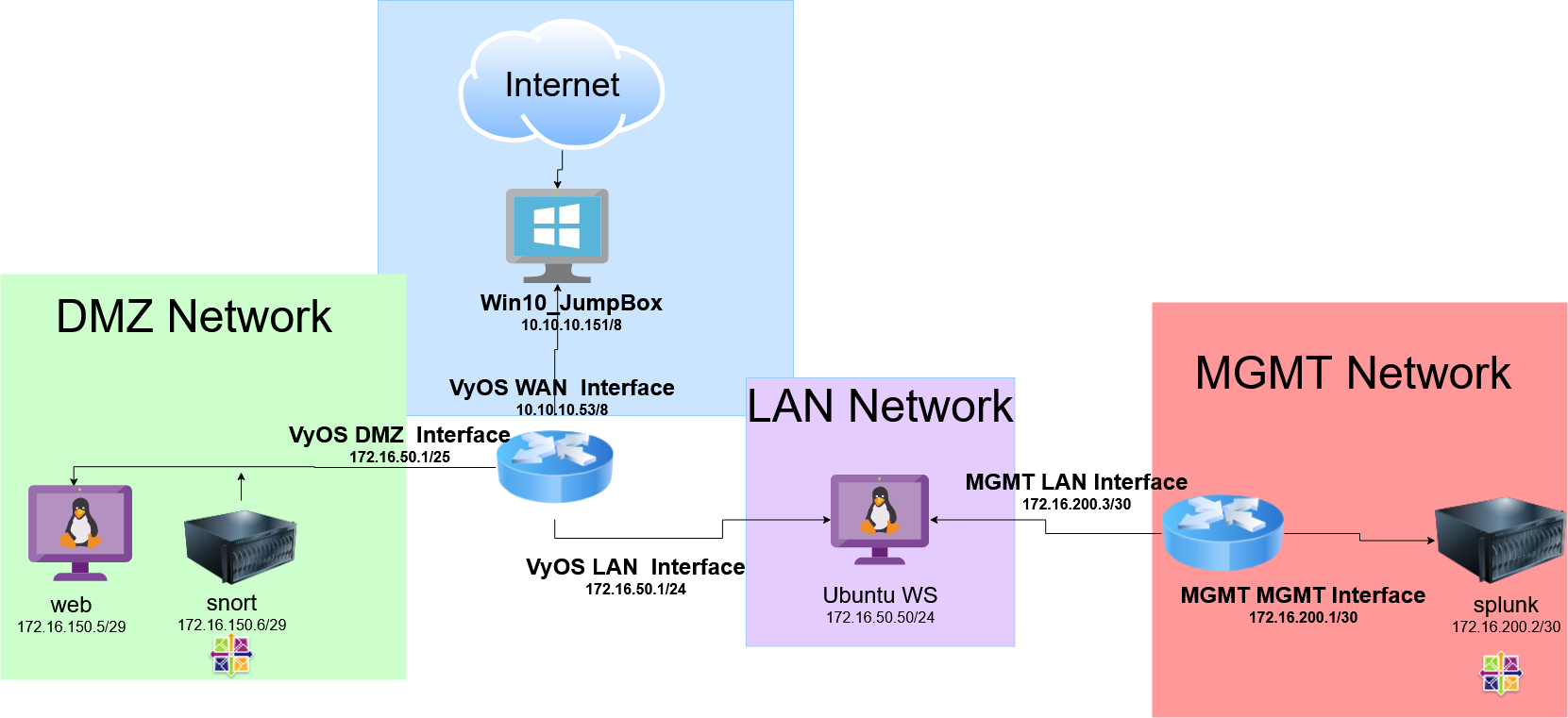
The documentation to set up your own Snort host and integrate it with Splunk is attached below! Overall, as large as this project ended up being and a bit overwhelming, this was really cool and taught me a lot about troubleshooting and Splunk’s capabilities. Also, we learned pretty quickly that the unstable VyOS ISO we were using was pretty unstable. Sometimes commands did not work and also, even if you commit your changes to the configuration file, you could not turn the server off without everything being wiped. You could thankfully restore from a snapshot with no issue, but the first time we reboot the server to find all of our networking configurations gone was interesting. The most important takeaway from this project was to remember to snapshot your VMs, something I’m guilty of not doing often enough!